How to know the password of a file
 There are several tools on the Internet, which allow you to find a secret password, or as we will call you today: The password Of a file, I do not intend with this post to promote malice; Rather explain the risk that exists to believe that all our data is protected simply behind the name of a fourth-grade love of the school.
There are several tools on the Internet, which allow you to find a secret password, or as we will call you today: The password Of a file, I do not intend with this post to promote malice; Rather explain the risk that exists to believe that all our data is protected simply behind the name of a fourth-grade love of the school.
In this case I will show the example of LasBit Corp, That if someone one day requires it because they forgot the name of which girlfriend used to protect their Excel file, or a malicious employee left behind a data set with malicious intent, here is an exit.
1. Bad password
It is clear that in this life we must use more than one password, for security; It is not possible to use it to access a forum just for making comments, than to enter our email account, Facebook or credit card. And this is what makes us lose our minds because sooner or later we can get confused.
The safest passwords are those with at least 9 digits, and which are not exact dictionary words, preferably containing numbers and, if possible, at least one capital letter. This, because the principles that programs follow to break a password are based on combinations of characters, the more they are, the longer it will be. It is not recommended to use other types of codes, such as words with accents or symbols because if one day we find a keyboard whose table of characters is broken ... the rush could have a taste of Chubby atoll.
2. Let's look at an example
This is the case of an Excel file that one of my technicians made to teach the use of the cadastral file. I have his permission, because he challenged me if he could find a way to break his password, so here we go:
As an Excel file, all you need is ExcelPassword and know the right way:
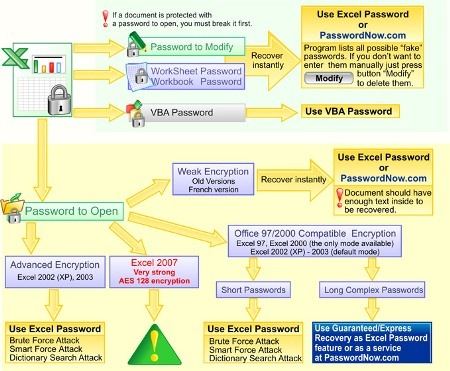
The chart shows the different routes:
- If all you want is to break the password of locked cells, but without having the file protected, there is an option called fake allowing Reset it Immediately without the program looking for the name.
- Another option is if you have an Excel file but 2003 versions, the Brute Force Attack I'd find it in a couple of minutes. Although those files also had the option of encryption, which if they had a long and complex password does not apply.
- And then there's the alternative of 2007 files, in which Office further complicated the way of encryption (AES 128 encryption), With which the work becomes slow to the extent that the password is long and complex.
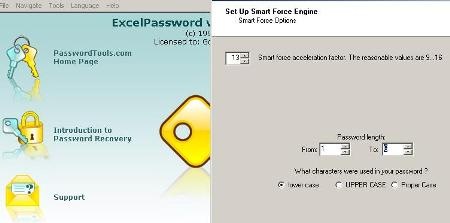
Following the wizzard, you can give some characteristics, such as the language in which you are expected to search for words, the maximum number of characters, initial and final word, if you want to consider capital letters or codes ... for each option shows the amount of time It can take the search from a couple of minutes to many days.
Knowing the technician, who could have placed words only in Spanish, and that according to calculation can be less than six characters, here I go.
Ready:
23 seconds without capitals
It must be the name of a school bride or the nickname of someone tucked into a closet. Hehe
It was so fast that I had no trouble getting the printscreen. The bad thing is that I didn't negotiate a bet, just a fucking challenge.
To test my theory, I used the same password for your Yahoo account, and ups !, it was the same although I warned you right now because I do not have any bad intentions with a technician for whose effort I have had many successes.
It is also possible that many are having chills at this time, and if they do not have them yet, check the list of passwords that can be found with the software LastBit.
3. What type of password can Break LastBit
It will not be the perfect world, but see that there are modules that can be purchased separately according to need: Among these are:
|
Office Documents
|
Internet Programs
Other files or programs
|
I do not doubt that these types of applications can be a solution to a business problem, as I mentioned at the beginning. But I have serious doubts if in the wrong hands it can be harmless.
Worried?